[root@www ~]#
cd /etc/pki/tls/certs
[root@www certs]#
make server.key
umask 77 ; \
/usr/bin/openssl genrsa -des3 1024 > server.key
Generating RSA private key, 1024 bit long modulus
.................................................. ....++++++
.............++++++
e is 61251 (0x10001)
Enter pass phrase:
// input pass phrase
Verifying - Enter pass phrase:
// verify
[root@www certs]#
// it's troublesome to input pass phrase always, so remove it from private key
[root@www certs]#
openssl rsa -in server.key -out server.key
Enter pass phrase for server.key:
// input pass phrase
writing RSA key
[root@www certs]#
[root@www certs]#
make server.csr
umask 77 ; \
/usr/bin/openssl req -utf8 -new -key server.key -out server.csr
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [GB]:
JP
State or Province Name (full name) [Berkshire]:
Hiroshima
Locality Name (eg, city) [Newbury]:
Hiroshima
Organization Name (eg, company) [My Company Ltd]:
Server Linux
Organizational Unit Name (eg, section) []:
IT Solution
Common Name (eg, your server's hostname) []:
www.server-linux.info
Email Address []:
root@server-linux.info
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:
// Enter with empty
An optional company name []:
// Enter with empty
[root@www certs]#
[root@www certs]#
openssl x509 -in server.csr -out server.crt -req -signkey server.key -days 3650
// make CertificateFile
Signature ok
subject=/C=JP/ST=Hiroshima/L=Hiroshima/O=Server Linux/OU=IT Solution/CN=www.server-linux.info/emailAddress=root@server-linux.info Getting Private key
[root@www certs]#
chmod 400 server.*
[root@www certs]#
[root@www certs]#
vi /etc/httpd/conf.d/ssl.conf
DocumentRoot "/var/www/html"
// line 84: make valid
ServerName
www.server-linux.info:443
// line 85: make valid and change
SSLCertificateFile
/etc/pki/tls/certs/server.crt
// line 112: change
SSLCertificateKeyFile
/etc/pki/tls/certs/server.key
// line 119: change
[root@www certs]#
/etc/rc.d/init.d/httpd restart
Stopping httpd:
[ OK ]
Starting httpd:
[ OK ]
Access to the page that is made in section (2) with https. Following window is shown because Certification File is not by CA. Click Ok to proceed.
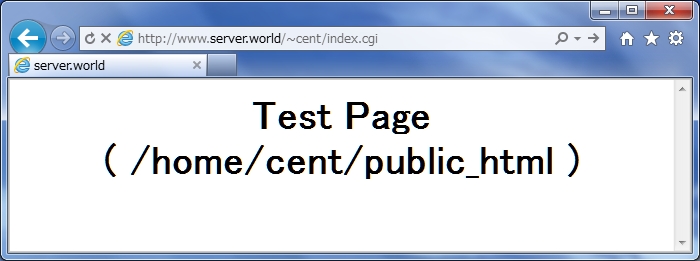 |
| Image test |
Completed to access. However, I think this is not so useful because always warning window is shown and visitors can not easily trust the server.
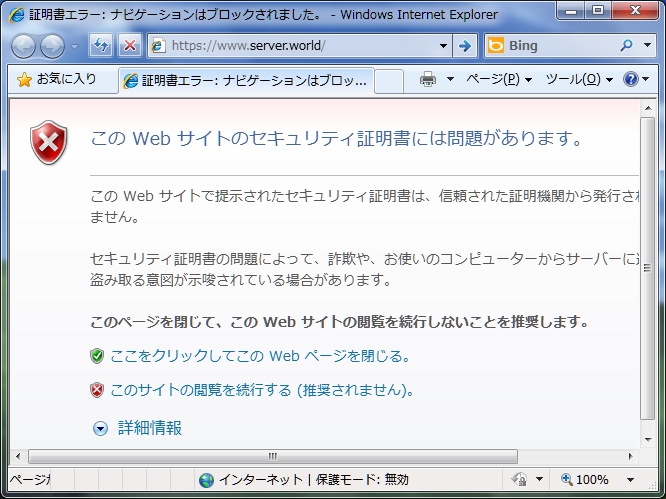 |
| Image test https |
No comments:
Post a Comment